OSPF, “Open Shortest Path First,” is a routing protocol that identifies the best way for data to move through a network. Authentication is key to OSPF because only authorized devices can share routing information and change the network. This blog post will look more closely at OSPF authentication and why it’s important.
Null authentication, cleartext password, a.k.a. simple password, and cryptographic authentication have always been supported by OSPFv2. Null represents no authentication. Cleartext provides a basic authentication method for preventing an OSPF router from accidentally being added to the network. OSPF neighbours can communicate securely, thanks to cryptographic authentication. This method allows neighbours to generate a hashed digest to ensure that each packet received was not tampered with during transit and was sent by a router permitted to participate in the OSPF domain. RFC 5709 introduces newer, more robust cryptographic authentication methods for OSPF.

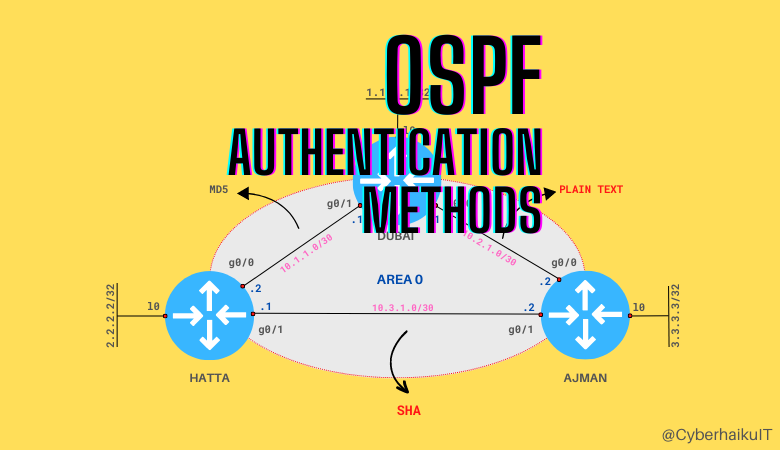
Let’s create a lab to investigate the OSPF authentication methods. I have placed three routers in OSPF area O and used the following authentication methods:
| Near End | Far End | Authentication | ||
| Router Name | Interface | Router Name | Interface | |
| Ajman | g0/0 | Dubai | g0/1 | Plain Text |
| Dubai | g0/0 | Hatta | g0/0 | MD5 |
| Hatta | g0/1 | Ajman | g0/1 | SHA |
Authentication Method: PLAIN TEXT
Let’s examine the plain text authentication first. This authentication method is configured between AJMAN and DUBAI routers.
Router : Dubai ! interface GigabitEthernet0/0 description [ Connected to Ajman router g0/0 ] ip ospf authentication ip ospf authentication-key DXB-AJMN !
Router : Ajman ! interface GigabitEthernet0/0 description [ Connected to Dubai router g0/0] ip ospf authentication ip ospf authentication-key DXB-AJMN !
Dubai#show ip ospf int gi0/0
GigabitEthernet0/0 is up, line protocol is up
Internet Address 10.2.1.1/30, Area 0, Attached via Interface Enable
Process ID 10, Router ID 1.1.1.1, Network Type BROADCAST, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State BDR, Priority 1
Designated Router (ID) 3.3.3.3, Interface address 10.2.1.2
Backup Designated router (ID) 1.1.1.1, Interface address 10.2.1.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:03
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/1/1, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 3
Last flood scan time is 1 msec, maximum is 4 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 3.3.3.3 (Designated Router)
Suppress hello for 0 neighbor(s)
Simple password authentication enabled
Dubai#
Ajman#show ip ospf int gi0/0
GigabitEthernet0/0 is up, line protocol is up
Internet Address 10.2.1.2/30, Area 0, Attached via Interface Enable
Process ID 10, Router ID 3.3.3.3, Network Type BROADCAST, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State DR, Priority 1
Designated Router (ID) 3.3.3.3, Interface address 10.2.1.2
Backup Designated router (ID) 1.1.1.1, Interface address 10.2.1.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:03
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/1/1, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 0, maximum is 2
Last flood scan time is 0 msec, maximum is 3 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 1.1.1.1 (Backup Designated Router)
Suppress hello for 0 neighbor(s)
Simple password authentication enabled
Ajman#
However, a packet capture from a router in Dubai reveals the password. Therefore, it is evident that in plain text authentication, the password is transmitted in plain text.

Authentication Method: MD5
Router : Dubai ! interface GigabitEthernet0/1 description [ Connected to Hatta router g0/0 ] ip address 10.1.1.1 255.255.255.252 ip ospf authentication message-digest ip ospf message-digest-key 1 md5 HATTA-DUBAI !
Router : Dubai ! interface GigabitEthernet0/0 ip address 10.1.1.2 255.255.255.252 ip ospf authentication message-digest ip ospf message-digest-key 1 md5 HATTA-DUBAI ip ospf 10 area 0
Hatta#show ip ospf int gi0/0
GigabitEthernet0/0 is up, line protocol is up
Internet Address 10.1.1.2/30, Area 0, Attached via Interface Enable
Process ID 10, Router ID 2.2.2.2, Network Type BROADCAST, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State DR, Priority 1
Designated Router (ID) 2.2.2.2, Interface address 10.1.1.2
Backup Designated router (ID) 1.1.1.1, Interface address 10.1.1.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:02
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/1/1, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 0, maximum is 2
Last flood scan time is 0 msec, maximum is 4 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 1.1.1.1 (Backup Designated Router)
Suppress hello for 0 neighbor(s)
Cryptographic authentication enabled
Youngest key id is 1
Dubai#show ip ospf int gi0/1
GigabitEthernet0/1 is up, line protocol is up
Internet Address 10.1.1.1/30, Area 0, Attached via Interface Enable
Process ID 10, Router ID 1.1.1.1, Network Type BROADCAST, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State BDR, Priority 1
Designated Router (ID) 2.2.2.2, Interface address 10.1.1.2
Backup Designated router (ID) 1.1.1.1, Interface address 10.1.1.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:00
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 3
Last flood scan time is 0 msec, maximum is 4 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 2.2.2.2 (Designated Router)
Suppress hello for 0 neighbor(s)
Cryptographic authentication enabled
Youngest key id is 1
Key id does not determine which is the youngest; the most recent key entered is the youngest. Therefore, if we wish to perform a rollover, we configure one side with the newer key, followed by the other side, and the adjacency will not flap.
What if authentication is enabled, but no key is configured?
The adjacency is displayed, although no key has been configured, and a default key is used.

However, the MD5 authentication key is not transmitted in plaintext. The specified key will be hashed with MD5 to produce a 128-bit hash value. Only this hash value will be checked on the other end.
MD5’s potential for message collisions when message hash codes are accidentally duplicated is a significant concern. Additionally, MD5 hash code strings are limited to 128 bits. This makes them more susceptible to compromise than subsequent hash code algorithms. to fix this issue,
Cisco began supporting HMAC-SHA in IOS 15.4(1)T, and OSPF also supports it (Hash Message Authentication Code Secure Hash Algorithm).
Authentication Method: SHA
Router : Hatta ! key chain Hatta-Ajman key 1 key-string Hatta-Ajman-PWD cryptographic-algorithm hmac-sha-512 ! interface GigabitEthernet0/1 ip address 10.3.1.1 255.255.255.252 ip ospf authentication key-chain Hatta-Ajman !
Router : Ajman ! key chain Hatta-Ajman key 1 key-string Hatta-Ajman-PWD cryptographic-algorithm hmac-sha-512 ! interface GigabitEthernet0/1 ip address 10.3.1.2 255.255.255.252 ip ospf authentication key-chain Hatta-Ajman
Ajman#show ip ospf int gi0/1
GigabitEthernet0/1 is up, line protocol is up
Internet Address 10.3.1.2/30, Area 0, Attached via Interface Enable
Process ID 10, Router ID 3.3.3.3, Network Type BROADCAST, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State DR, Priority 1
Designated Router (ID) 3.3.3.3, Interface address 10.3.1.2
Backup Designated router (ID) 2.2.2.2, Interface address 10.3.1.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:08
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 1 msec, maximum is 6 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 2.2.2.2 (Backup Designated Router)
Suppress hello for 0 neighbor(s)
Cryptographic authentication enabled
Sending SA: Key 1, Algorithm HMAC-SHA-512 - key chain Hatta-Ajman
Hatta#show ip ospf int gig0/1
GigabitEthernet0/1 is up, line protocol is up
Internet Address 10.3.1.1/30, Area 0, Attached via Interface Enable
Process ID 10, Router ID 2.2.2.2, Network Type BROADCAST, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State BDR, Priority 1
Designated Router (ID) 3.3.3.3, Interface address 10.3.1.2
Backup Designated router (ID) 2.2.2.2, Interface address 10.3.1.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:07
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 1 msec, maximum is 5 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 3.3.3.3 (Designated Router)
Suppress hello for 0 neighbor(s)
Cryptographic authentication enabled
Sending SA: Key 1, Algorithm HMAC-SHA-512 - key chain Hatta-Ajman

Final configuration

!
hostname Dubai
!
router ospf 10
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
ip ospf 10 area 0
!
interface GigabitEthernet0/0
ip address 10.2.1.1 255.255.255.252
ip ospf authentication
ip ospf authentication-key DXB-AJMN
ip ospf 10 area 0
!
interface GigabitEthernet0/1
ip address 10.1.1.1 255.255.255.252
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 HATTA-DUBAI
ip ospf 10 area 0
!
!
!
hostname Hatta
!
router ospf 10
!
key chain Hatta-Ajman
key 1
key-string Hatta-Ajman-PWD
cryptographic-algorithm hmac-sha-512
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
ip ospf 10 area 0
!
interface GigabitEthernet0/0
ip address 10.1.1.2 255.255.255.252
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 HATTA-DUBAI
ip ospf 10 area 0
!
interface GigabitEthernet0/1
ip address 10.3.1.1 255.255.255.252
ip ospf authentication key-chain Hatta-Ajman
ip ospf 10 area 0
!
!
hostname Ajman
!
router ospf 10
!
key chain Hatta-Ajman
key 1
key-string Hatta-Ajman-PWD
cryptographic-algorithm hmac-sha-512
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
ip ospf 10 area 0
!
interface GigabitEthernet0/0
ip address 10.2.1.2 255.255.255.252
ip ospf authentication
ip ospf authentication-key DXB-AJMN
ip ospf 10 area 0
!
interface GigabitEthernet0/1
ip address 10.3.1.2 255.255.255.252
ip ospf authentication key-chain Hatta-Ajman
ip ospf 10 area 0




Interesting Article and really informative.Keep posting more